
░▒▓█ Introduction
I've been making php static code analysis tool for a while and few months ago I ran it against ~1000 (more or less) top wordpress plugins.
Scanning results were manually verified in my spare time and delivered to official plugins@wordpress.org from 04.07.2015 to 31.08.2015. Most of reported plugins are already patched, some are not. Vulnerable and not patched plugins are already removed from official wordpress plugin repository.
░▒▓█ Results
103 plugins vulnerable with more than 4.000.000 active installations in total (~30.000.000 downloads)
List of reported plugins (original reports contain verification/reproduce sections and urls to plugin wordpress repository entries, where you can also verify changelog) :
- Cross-Site Scripting (XSS) in Duplicator 0.5.24 [original report - Sat, 15 Aug 2015]
- Cross-Site Scripting (XSS) in All In One WP Security 3.9.7 [original report - Thu, 13 Aug 2015]
- Cross-Site Scripting (XSS) in AddThis 5.0.12 [original report - Tue, 11 Aug 2015]
- Cross-Site Scripting (XSS) in Display Widgets 2.03 [original report - Tue, 11 Aug 2015]
- Blind SQL injection and XSS in SEO SearchTerms Tagging 2 1.535 [original report - Wed, 8 Jul 2015] NOT PATCHED
- Blind SQL injection in Pretty Link Lite 1.6.7 [original report - Wed, 8 Jul 2015]
- Blind SQL injection in WP Statistics 9.4 [original report - Thu, 9 Jul 2015]
- Cross-Site Scripting (XSS) in My Page Order 4.3 [original report - Thu, 13 Aug 2015] NOT PATCHED
- Cross-Site Scripting (XSS) in Category Order and Taxonomy Terms Order 1.4.4 [original report - Tue, 18 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in WP Social Bookmarking Light 1.7.9 [original report - Wed, 19 Aug 2015]
- Cross-Site Scripting (XSS) in WP Google Fonts v3.1.3 [original report - Wed, 19 Aug 2015]
- Cross-Site Scripting (XSS) in Easy Table 1.5.2 [original report - Mon, 10 Aug 2015]
- Cross-Site Scripting (XSS) in My Category Order 4.3 [original report - Thu, 13 Aug 2015] NOT PATCHED
- Cross-Site Scripting (XSS) in CKEditor for WordPress 4.5.3 [original report - Mon, 31 Aug 2015]
- Blind SQL injection in Huge IT Slider 2.8.6 [original report - Wed, 22 Jul 2015]
- Cross-Site Scripting (XSS) in Dynamic Widgets 1.5.10 [original report - Tue, 11 Aug 2015]
- Cross-Site Scripting (XSS) in Google Language Translator 4.0.9 [original report - Thu, 13 Aug 2015]
- Cross-Site Scripting (XSS) in JW Player 6 Plugin for Wordpress 2.1.14 [original report - Wed, 19 Aug 2015] NOT PATCHED
- Persistent Cross-Site Scripting (XSS) in Floating Social Media Icon 2.1 [original report - Wed, 19 Aug 2015]
- Blind SQL injections in Contact Form Builder 1.0.24 [original report - Tue, 7 Jul 2015]
- Arbitrary file upload and Cross-Site Scripting (XSS) in Slideshow Gallery 1.5.3 [original report - Thu, 20 Aug 2015]
- Blind SQL injection in Master Slider 2.5.1 [original report - Thu, 20 Aug 2015]
- Blind SQL injection and Reflected XSS in WP RSS Multi Importer 3.15 [original report - Wed, 8 Jul 2015] NOT PATCHED
- Cross-Site Scripting (XSS) in Add Link to Facebook 2.2.7 [original report - Thu, 13 Aug 2015] NOT PATCHED
- Blind SQL injection in 404 to 301 2.0.2 [original report - Thu, 20 Aug 2015]
- Cross-Site Scripting (XSS) in Alpine PhotoTile for Instagram 1.2.7.5 [original report - Thu, 20 Aug 2015]
- Cross-Site Scripting (XSS) in Huge IT Image Gallery 1.5.1 [original report - Thu, 20 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in Visitor Maps and Who's Online 1.5.8.6 [original report - Thu, 20 Aug 2015]
- Cross-Site Scripting (XSS) in WP Google Map Plugin 2.3.9 [original report - Thu, 20 Aug 2015]
- Cross-Site Scripting (XSS) in WP Job Manager 1.23.7 [original report - Thu, 20 Aug 2015]
- SQL injection (+XSS) in Easy Social Icons 1.2.3.1 [original report - Wed, 22 Jul 2015]
- Cross-Site Scripting (XSS) in My Link Order 4.3 [original report - Thu, 13 Aug 2015] NOT PATCHED
- Persistent Cross-Site Scripting (XSS) in WP Database Backup 3.3 [original report - Thu, 20 Aug 2015]
- Arbitrary file upload and Reflected Cross-Site Scripting (XSS) in Theme Test Drive 2.9 [original report - Thu, 20 Aug 2015]
- Cross-Site Scripting (XSS) in Subscribe to Comments Reloaded 150611 [original report - Thu, 20 Aug 2015]
- Cross-Site Scripting (XSS) in SEO Redirection 2.8 [original report - Fri, 21 Aug 2015]
- Cross-Site Scripting (XSS) in qTranslate-X 3.4.3 [original report - Fri, 21 Aug 2015]
- Blind SQL injection in Gallery Bank Lite Edition Version 3.0.229 [original report - Fri, 21 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in Crazy Bone 0.5.5 [original report - Fri, 21 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in Social Media Widget by Acurax 2.2 [original report - Fri, 21 Aug 2015]
- Reflected Cross-Site Scripting (XSS) in Anti-spam by CleanTalk 5.21 [original report - Tue, 25 Aug 2015]
- Blind SQL injection in Smooth Slider 2.6.5 [original report - Wed, 15 Jul 2015]
- Cross-Site Scripting (XSS) in YITH Maintenance Mode 1.1.4 [original report - Fri, 21 Aug 2015]
- Multiple SQL injections and XSS in Email Subscribers 2.9 [original report - Mon, 10 Aug 2015]
- Cross Site Scripting (XSS) in Email newsletter 20.13.6 [original report - Mon, 10 Aug 2015] NOT PATCHED
- Cross-Site Scripting (XSS) in Easy Pie Coming Soon 1.0.0 [original report - Mon, 10 Aug 2015]
- Cross-Site Scripting (XSS) in Easy Pie Coming Soon 1.0.0 [original report - Mon, 10 Aug 2015]
- Cross-Site Scripting (XSS) in Contact Bank Lite Edition 2.0.225 [original report - Thu, 13 Aug 2015]
- Cross-Site Scripting (XSS) in Kiwi Logo Carousel 1.7.1 [original report - Thu, 13 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in WP Legal Pages 1.0.1 [original report - Fri, 21 Aug 2015]
- Cross-Site Scripting (XSS) in WP Crontrol 1.2.3 [original report - Fri, 21 Aug 2015]
- Cross-Site Scripting (XSS) in Websimon Tables 1.3.4 [original report - Fri, 21 Aug 2015] NOT PATCHED
- Cross-Site Scripting (XSS) in SEO Rank Reporter 2.2.2 [original report - Mon, 24 Aug 2015] NOT PATCHED
- Persistent Cross-Site Scripting (XSS) in WP Keyword Link 1.7 [original report - Mon, 24 Aug 2015] NOT PATCHED
- Cross-Site Scripting (XSS) in Huge IT Portfolio Gallery 1.5.7 [original report - Mon, 24 Aug 2015]
- Cross-Site Scripting (XSS) in Manual Image Crop 1.10 [original report - Mon, 24 Aug 2015]
- Cross-Site Scripting (XSS) in iQ Block Country in 1.1.19 [original report - Mon, 24 Aug 2015]
- SQL injection and Cross-Site Scripting (XSS) in GigPress 2.3.10 [original report - Mon, 24 Aug 2015]
- Arbitrary file read in Multi Plugin Installer 1.1.0 [original report - Mon, 24 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in FV Wordpress Flowplayer 6.0.3.3 [original report - Mon, 24 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in Easy Coming Soon 1.8.1 [original report - Mon, 24 Aug 2015]
- Cross-Site Scripting (XSS) in Contact Form Manager 1.4.1 [original report - Mon, 24 Aug 2015] NOT PATCHED
- Blind SQL injection in WordPress Meta Robots 2.1 [original report - Tue, 25 Aug 2015] NOT PATCHED
- Cross-Site Scripting (XSS) in Smart Slider 2 2.3.11 [original report - Wed, 26 Aug 2015]
- Cross-Site Scripting (XSS) in Soundcloud is Gold 2.3.1 [original report - Wed, 26 Aug 2015]
- Blind SQL injection in Contact Form Maker 1.7.30 [original report - Wed, 8 Jul 2015]
- Cross-Site Scripting (XSS) in Plugin Central 2.5 [original report - Tue, 25 Aug 2015]
- Blind SQL injection in yet another stars rating 0.9.0 [original report - Mon, 6 Jul 2015]
- Blind SQL injection in smart manager for wp e commerce 3.9.6 [original report - Wed, 8 Jul 2015]
- Blind SQL injection and CSRF for logged administrators in awesome filterable portfolio 1.8.6 [original report - Tue, 7 Jul 2015]
- Blind SQL injections in WP Shop 3.4.3.15 [original report - Wed, 8 Jul 2015]
- Cross-Site Scripting (XSS) in Job Manager 0.7.24 [original report - Tue, 25 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in "Post video players, slideshow albums, photo galleries and music / podcast playlist" 1.136 [original report - Tue, 25 Aug 2015]
- Arbitrary file modification in Child Theme Creator by Orbisius 1.2.6 [original report - Wed, 8 Jul 2015]
- SQL injection in WP-Stats-Dashboard 2.9.4 [original report - Tue, 25 Aug 2015] NOT PATCHED
- Cross-Site Scripting (XSS) in WP Page Widget 2.7 [original report - Tue, 25 Aug 2015]
- Blind SQL injection in wti like post 1.4.2 [original report - Sun, 5 Jul 2015]
- SQL injection in Huge IT Google Map 2.2.5 [original report - Wed, 8 Jul 2015] NOT PATCHED
- Blind SQL injection and Reflected XSS vulnerabilities in broken link manager plugin 0.4.5 [original report - Sat, 4 Jul 2015]
- Blind SQL injection in Microblog Poster 1.6.0 [original report - Wed, 22 Jul 2015]
- SQL injection and Cross-Site Scripting (XSS) in GoCodes 1.3.5 [original report - Tue, 25 Aug 2015] NOT PATCHED
- Blind SQL injections in Auto Affiliate Links 4.9.9.4 [original report - Wed, 15 Jul 2015]
- Cross-Site Scripting (XSS) in WP Widget Cache 0.26 [original report - Tue, 25 Aug 2015] NOT PATCHED
- SQL injections and XSS in SendPress Newsletters 1.1.7.21 [original report - Thu, 23 Jul 2015]
- Cross-Site Scripting (XSS) in Email Users 4.7.5 [original report - Mon, 10 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in Social Share Button 2.1 [original report - Tue, 25 Aug 2015] NOT PATCHED
- Cross-Site Scripting (XSS) in Social Locker | BizPanda 4.2.0 [original report - Tue, 25 Aug 2015]
- Cross Site Scripting (XSS) in Email Encoder Bundle - Protect Email Address 1.4.1 [original report - Mon, 10 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in Page Restrict 2.2.1 [original report - Tue, 25 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in Multicons 2.1 [original report - Tue, 25 Aug 2015]
- Persistent Cross-Site Scripting (XSS) in PlugNedit Adaptive Editor 5.2.0 [original report - Tue, 25 Aug 2015]
- Blind SQL injection in WooCommerce Abandon Cart Lite Plugin 1.7 [original report - Wed, 15 Jul 2015]
- Persistent XSS in Broken Link manager Ver 0.5.5 [original report - Thu, 16 Jul 2015]
- Blind SQL injections in Quiz Master Next 4.4.2 [original report - Thu, 16 Jul 2015]
- Cross-Site Scripting (XSS) in Role Scoper 1.3.64 [original report - Wed, 26 Aug 2015]
- Blind SQL injections in NEX-Forms 4.0 [original report - Thu, 16 Jul 2015]
- Cross-Site Scripting (XSS) in Ad Inserter 1.5.5 [original report - Thu, 13 Aug 2015]
- Cross-Site Scripting (XSS) in Olevmedia Shortcodes 1.1.8 [original report - Tue, 25 Aug 2015]
- Blind SQL injection in Booking System (+WooCommerce) 2.0 [original report - Tue, 7 Jul 2015]
- Blind SQL injections in Plgumatter Optin Feature Box 2.0.13 [original report - Thu, 16 Jul 2015]
- Blind SQL injection in WR ContactForm 1.1.9 [original report - Thu, 9 Jul 2015]
- Cross-Site Scripting (XSS) in Simple Fields 1.4.10 [original report - Tue, 25 Aug 2015]
- Blind SQL injections, XSS and more in wp live chat support 4.3.5 [original report - Mon, 6 Jul 2015]
Some notes:
Without magic_quotes_gpc (wordpress "emulate" it anyway when it's off) it will be some more exploitable SQLi vulnerabilities.
I'm also pretty sure that there are some vulnerabilities in reports that I missed, or just thought that they were unexploitable.
Because of low resources limits (like memory limit ~3GB) many plugins from top 1000 list didn't get 100% code coverage.
░▒▓█ What about CVE identifiers?
I've sent bulk request to cve-assign@mitre.org recently. No response so far.
░▒▓█ Static code analysis tool and some hilights
I used own PhpSourcerer static code analysis tool, which is still in development. You can try PhpSourcerer yourself on php-grinder.com (current limits: 2GB Ram, 15 minutes execution time). It has nice web-ui instead of raw text file reports:
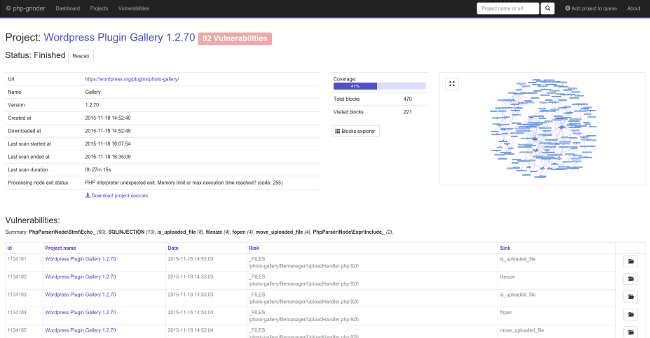
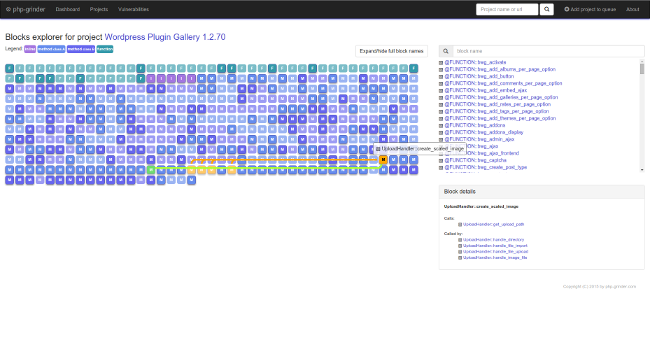
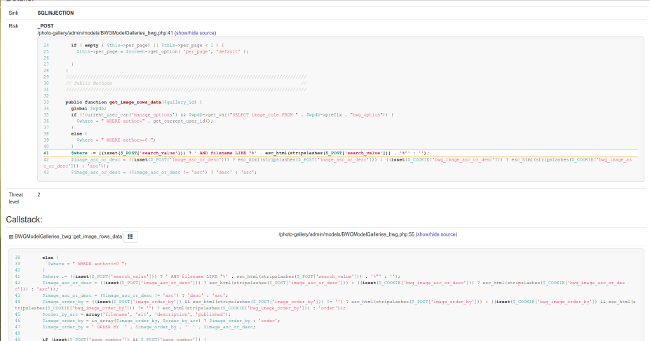
I show you some details about reported vulnerabilities to demonstrate what this tool is capable of.
◼ Reflected Cross-Site Scripting (XSS) in Simple Fields 1.4.10
Description: Authenticated users (like subscribers) can inject html/js code (there is no CSRF protection!)
Some urls: Sent report | Original project sources | PhpSourcerer output
This is a simple example, so I guess it doesn't need explanation:
...
function field_type_post_dialog_load() {
global $sf;
$arr_enabled_post_types = isset($_POST["arr_enabled_post_types"]) ? $_POST["arr_enabled_post_types"] : array();
$str_enabled_post_types = isset($_POST["str_enabled_post_types"]) ? $_POST["str_enabled_post_types"] : "";
$additional_arguments = isset($_POST["additional_arguments"]) ? $_POST["additional_arguments"] : "";
$existing_post_types = get_post_types(NULL, "objects");
$selected_post_type = isset($_POST["selected_post_type"]) ? (string) $_POST["selected_post_type"] : "";
if (empty($arr_enabled_post_types)) {
$arr_enabled_post_types = explode(",", $str_enabled_post_types);
}
/*echo "<br>selected_post_type: $selected_post_type";
echo "<br>str_enabled_post_types: $str_enabled_post_types";
echo "<br>enabled post types:"; print_r($arr_enabled_post_types);*/
// If no post type is selected then don't show any posts
if (empty($arr_enabled_post_types)) {
_e("<p>No post type is selected. Please at at least one post type in Simple Fields.</p>", "simple-fields");
exit;
}
?>
<?php if (count($arr_enabled_post_types) > 1) { ?>
<p>Show posts of type:</p>
<ul class="simple-fields-meta-box-field-group-field-type-post-dialog-post-types">
<?php
$loopnum = 0;
foreach ($existing_post_types as $key => $val) {
if (!in_array($key, $arr_enabled_post_types)) {
continue;
}
if (empty($selected_post_type) && $loopnum == 0) {
$selected_post_type = $key;
}
$class = "";
if ($selected_post_type == $key) {
$class = "selected";
}
printf("\n<li class='%s'><a href='%s'>%s</a></li>", $class, "$key", $val->labels->name);
$loopnum++;
}
?>
</ul>
<?php
} else {
$selected_post_type = $arr_enabled_post_types[0];
?>
<p>Showing posts of type: <a href="<?php echo $selected_post_type; ?>"><?php echo $existing_post_types[$selected_post_type]->labels->name; ?></a></p>
<?php
} ?>
...
◼ Blind SQL injection in smart manager for wp e commerce 3.9.6
Description: Unauthenticated remote attackers can execute arbitrary SQL commands.
Some urls: Sent report | Original project sources | PhpSourcerer output
/smart-manager-for-wp-e-commerce/sm/woo-json.php:
<?php
ob_start();
...
// For insert updating product in woo.
if (isset ( $_POST ['cmd'] ) && $_POST ['cmd'] == 'saveData') {
...
if ( $_POST['active_module'] == "Coupons" ) {
...
} else {
$result = woo_insert_update_data ( $_POST );
}
...
woo_insert_update_data() :
...
function woo_insert_update_data($post) {
global $wpdb,$woocommerce;
$_POST = $post;
// Fix: PHP 5.4
$editable_fields = array(
'_billing_first_name' , '_billing_last_name' , '_billing_email', '_billing_address_1', '_billing_address_2', '_billing_city', '_billing_state',
'_billing_country','_billing_postcode', '_billing_phone',
'_shipping_first_name', '_shipping_last_name', '_shipping_address_1', '_shipping_address_2',
'_shipping_city', '_shipping_state', '_shipping_country','_shipping_postcode', 'order_status'
);
$new_product = json_decode($_POST['edited']);
$edited_prod_ids = array();
$edited_prod_slug = array();
if (!empty($new_product)) {
foreach($new_product as $product) {
$edited_prod_ids[] = $product->id;
}
}
//Code for getting the product slugs
if ( !empty($edited_prod_ids) ) {
$query_prod_slug = "SELECT id, post_name
FROM {$wpdb->prefix}posts
WHERE id IN (".implode(",",$edited_prod_ids).")";
$results_prod_slug = $wpdb->get_results($query_prod_slug, 'ARRAY_A');
$prod_slug_rows = $wpdb->num_rows;
...
So we can inject our payload in valid json variable, like in verification example in sent report:
curl --request POST --data "cmd=saveData&edited=[{\"id\":\" 1) union select sleep(10),2; -- -\"}]" http://localhost/wp-content/plugins/smart-manager-for-wp-e-commerce/sm/woo-json.php
◼ Reflected Cross-Site Scripting (XSS) in SEO Redirection 2.8
Description: Authenticated administrators can inject html/js code (there is no CSRF protection).
Some urls: Sent report | Original project sources | PhpSourcerer output
/options/option_page_post_redirection_list.php:
<?php
global $wpdb,$table_prefix,$util;
$table_name = $table_prefix . 'WP_SEO_Redirection';
if($util->get('del')!='')
{
$delid=intval($util->get('del'));
$wpdb->query(" delete from $table_name where ID='$delid' ");
if($util->there_is_cache()!='')
$util->info_option_msg("You have a cache plugin installed <b>'" . $util->there_is_cache() . "'</b>, you have to clear cache after any changes to get the changes reflected immediately! ");
$SR_redirect_cache = new clogica_SR_redirect_cache();
$SR_redirect_cache->free_cache();
}
$rlink=$util->get_current_parameters(array('del','search','page_num','add','edit'));
?>
<br/>
<script type="text/javascript">
...
</script>
<div class="link_buttons">
<table border="0" width="100%">
<tr>
<td width="110"><a href="<?php echo $rlink?>&add=1"><div class="add_link">Add New</div></a></div></td>
<td align="right">
<input onkeyup="if (event.keyCode == 13) go_search();" style="height: 30px;" id="search" type="text" name="search" value="<?php echo $util->get('search')?>" size="40">
<a onclick="go_search()" href="#"><div class="search_link">Search</div></a>
$util is object of "clogica_util" class (seo-redirection.php):
<?php
/*
...
*/
require_once ('common/controls.php');
require_once ('custom/controls.php');
require_once ('custom/controls/cf.SR_redirect_cache.class.php');
if(!defined('WP_SEO_REDIRECTION_OPTIONS'))
{
define( 'WP_SEO_REDIRECTION_OPTIONS', 'wp-seo-redirection-group' );
}
if(!defined('WP_SEO_REDIRECTION_VERSION'))
{
define( 'WP_SEO_REDIRECTION_VERSION', '2.8');
}
$util= new clogica_util();
$util->set_option_gruop(WP_SEO_REDIRECTION_OPTIONS);
...
Finally lets look how clogica_util::get() looks like:
...
public function get($key,$type='text')
{
if(array_key_exists($key,$_GET))
{
$unsafe_val=$_GET[$key];
return $this->sanitize_req($unsafe_val,$type);
}
else
{
return '';
}
}
...
public function sanitize_req($unsafe_val,$type='text')
{
switch ($type) {
case 'text': return sanitize_text_field($unsafe_val);
break;
case 'int': return intval($unsafe_val);
break;
case 'email': return sanitize_email($unsafe_val);
break;
case 'filename': return sanitize_file_name($unsafe_val);
break;
case 'title': return sanitize_title($unsafe_val);
break;
default:
return sanitize_text_field($unsafe_val);
}
}
...
Yep. Wordpress sanitize_text_field() doesn't prevent from succesful XSS exploitation in html tag attribute.
◼ Reflected Cross-Site Scripting (XSS) in Display Widgets 2.03
Description: Authenticated users (like subscribers) can inject html/js code (there is no CSRF protection!).
Some urls: Sent report | Original project sources | PhpSourcerer output
Lets look at the DWPlugin::show_widget_options() method (invokes by http://localhost/wp-admin/admin-ajax.php?action=dw_show_widget)
...
function show_widget_options() {
$instance = htmlspecialchars_decode(nl2br(stripslashes($_POST['opts'])));
$instance = json_decode($instance, true);
$this->id_base = $_POST['id_base'];
$this->number = $_POST['widget_number'];
$new_instance = array();
$prefix = 'widget-'. $this->id_base .'['. $this->number .'][';
foreach ( $instance as $k => $v ) {
$n = str_replace( array( $prefix, ']'), '', $v['name']);
$new_instance[$n] = $v['value'];
}
self::show_hide_widget_options($this, '', $new_instance);
die();
}
...
As we can see we have two variables assigned to object properties, and then another method (show_hide_widget_options) is called with $this argument. DWPlugin::show_hide_widget_options():
...
function show_hide_widget_options($widget, $return, $instance) {
self::register_globals();
$wp_page_types = self::page_types();
$instance['dw_include'] = isset($instance['dw_include']) ? $instance['dw_include'] : 0;
$instance['dw_logged'] = self::show_logged($instance);
$instance['other_ids'] = isset($instance['other_ids']) ? $instance['other_ids'] : '';
?>
<p>
<label for="<?php echo $widget->get_field_id('dw_include'); ?>"><?php _e('Show Widget for:', 'display-widgets') ?></label>
<select name="<?php echo $widget->get_field_name('dw_logged'); ?>" id="<?php echo $widget->get_field_id('dw_logged'); ?>" class="widefat">
<option value=""><?php _e('Everyone', 'display-widgets') ?></option>
<option value="out" <?php echo selected( $instance['dw_logged'], 'out' ) ?>><?php _e('Logged-out users', 'display-widgets') ?></option>
<option value="in" <?php echo selected( $instance['dw_logged'], 'in' ) ?>><?php _e('Logged-in users', 'display-widgets') ?></option>
</select>
</p>
<p>
<select name="<?php echo $widget->get_field_name('dw_include'); ?>" id="<?php echo $widget->get_field_id('dw_include'); ?>" class="widefat">
...
And finally get_field_id method and get_field_name:
...
function get_field_name($field_name) {
return 'widget-' . $this->id_base . '[' . $this->number . '][' . $field_name . ']';
}
function get_field_id($field_name) {
return 'widget-' . $this->id_base . '-' . $this->number . '-' . $field_name;
}
...
$this->id_base and $this->number were assigned at the beggining in DWPlugin::show_widget_options method.
◼ Persistent Cross-Site Scripting (XSS) in FV Wordpress Flowplayer 6.0.3.3
Description: Authenticated administrators can store html/js code in plugin configuration values (there is no CSRF protection!)
Some urls: Sent report | Original project sources | PhpSourcerer output
First lets look at fv_wp_flowplayer_admin_init() function:
...
function fv_wp_flowplayer_admin_init() {
if( isset($_GET['type']) ) {
if( $_GET['type'] == 'fvplayer_video' || $_GET['type'] == 'fvplayer_video_1' || $_GET['type'] == 'fvplayer_video_2' || $_GET['type'] == 'fvplayer_mobile' ) {
$_GET['post_mime_type'] = 'video';
}
else if( $_GET['type'] == 'fvplayer_splash' || $_GET['type'] == 'fvplayer_logo' ) {
$_GET['post_mime_type'] = 'image';
}
}
if( isset($_POST['fv-wp-flowplayer-submit']) ) {
global $fv_fp;
if( method_exists($fv_fp,'_set_conf') ) {
$fv_fp->_set_conf();
} else {
echo 'Error saving FV Flowplayer options.';
}
}
global $fv_fp;
...
As we can see we execute _set_conf() method on $fv_wp object when we send fv-wp-flowplayer-submit in POST. $fv_fp is global object of flowplayer_frontend class defined in flowplayer.php main file.
...
$fv_wp_flowplayer_ver = '2.3.17';
$fv_wp_flowplayer_core_ver = '5.5.2';
include( dirname( __FILE__ ) . '/includes/extra-functions.php' );
if( file_exists( dirname( __FILE__ ) . '/includes/module.php' ) ) {
include( dirname( __FILE__ ) . '/includes/module.php' );
}
include( dirname( __FILE__ ) . '/models/checker.php' );
$FV_Player_Checker = new FV_Player_Checker();
include_once(dirname( __FILE__ ) . '/models/flowplayer.php');
include_once(dirname( __FILE__ ) . '/models/flowplayer-frontend.php');
$fv_fp = new flowplayer_frontend();
if( is_admin() ) {
include( dirname( __FILE__ ) . '/controller/backend.php' );
register_deactivation_hook( __FILE__, 'flowplayer_deactivate' );
}
include( dirname( __FILE__ ) . '/controller/frontend.php' );
require_once( dirname( __FILE__ ) . '/controller/shortcodes.php');
$fv_fp->_set_conf() method is not really belongs to "flowplayer_frontend" class but to "flowplayer" that "flowplayer_frontend" is extending:
...
class flowplayer_frontend extends flowplayer {
...
flowplayer::_set_conf():
...
public function _set_conf() {
$aNewOptions = $_POST;
$sKey = $aNewOptions['key'];
foreach( $aNewOptions AS $key => $value ) {
if( is_array($value) ) {
$aNewOptions[$key] = $value;
} else if( !in_array( $key, array('amazon_region', 'amazon_bucket', 'amazon_key', 'amazon_secret', 'font-face', 'ad', 'ad_css') ) ) {
$aNewOptions[$key] = trim( preg_replace('/[^A-Za-z0-9.:\-_\/]/', '', $value) );
} else {
$aNewOptions[$key] = stripslashes($value);
}
if( (strpos( $key, 'Color' ) !== FALSE )||(strpos( $key, 'canvas' ) !== FALSE)) {
$aNewOptions[$key] = '#'.strtolower($aNewOptions[$key]);
}
}
$aNewOptions['key'] = trim($sKey);
$aOldOptions = is_array(get_option('fvwpflowplayer')) ? get_option('fvwpflowplayer') : array();
if( isset($aNewOptions['db_duration']) && $aNewOptions['db_duration'] == "true" && ( !isset($aOldOptions['db_duration']) || $aOldOptions['db_duration'] == "false" ) ) {
global $FV_Player_Checker;
$FV_Player_Checker->queue_add_all();
}
if( !isset($aNewOptions['pro']) || !is_array($aNewOptions['pro']) ) {
$aNewOptions['pro'] = array();
}
if( !isset($aOldOptions['pro']) || !is_array($aOldOptions['pro']) ) {
$aOldOptions['pro'] = array();
}
$aNewOptions['pro'] = array_merge($aOldOptions['pro'],$aNewOptions['pro']);
$aNewOptions = array_merge($aOldOptions,$aNewOptions);
$aNewOptions = apply_filters( 'fv_flowplayer_settings_save', $aNewOptions, $aOldOptions );
update_option( 'fvwpflowplayer', $aNewOptions );
$this->conf = $aNewOptions;
$this->css_writeout();
return true;
}
...
As we can see we override plugin options, that is why we can inject XSS payload in fv_flowplayer_admin_default_options():
...
function fv_flowplayer_admin_default_options() {
global $fv_fp;
?>
<table class="form-table2">
...
<tr>
<td><label for="width">Default video size [px]:</label></td>
<td colspan="2">
<label for="width">W:</label> <input type="text" class="small" name="width" id="width" value="<?php echo trim($fv_fp->conf['width']); ?>" />
<label for="height">H:</label> <input type="text" class="small" name="height" id="height" value="<?php echo trim($fv_fp->conf['height']); ?>" />
</td>
</tr>
<tr>
<td><label for="googleanalytics">Google Analytics ID:</label></td>
<td colspan="3"><input type="text" name="googleanalytics" id="googleanalytics" value="<?php echo trim($fv_fp->conf['googleanalytics']); ?>" /></td>
</tr>
<tr>
<td><label for="key">Commercial License Key:</label></td>
<td colspan="3"><input type="text" name="key" id="key" value="<?php echo trim($fv_fp->conf['key']); ?>" /></td>
</tr>
...
◼ Blind SQL injection in Master Slider 2.5.1
Description: Authenticated users (like editors) can execute arbitrary sql commands (there is no CSRF protection)
Some urls: Sent report | Original project sources | PhpSourcerer output
I'll just show you just the flow without commenting (pay attention to orderby parameter/variables). We start by looking at /master-slider/admin/views/slider-dashboard/list-sliders.php file:
<?php
msp_get_panel_header();
// Display sliders list
$slider_table_list = new MSP_List_Table();
$slider_table_list->prepare_items();
$slider_table_list->display();
MSP_List_Table::prepare_items() :
...
function prepare_items() {
$columns = $this->get_columns();
$hidden = array();
$sortable = $this->get_sortable_columns();
$this->_column_headers = array( $columns, $hidden, $sortable );
$this->process_bulk_action();
$perpage = (int) apply_filters( 'masterslider_admin_sliders_per_page', 10 );
$current_page = $this->get_pagenum();
$orderby = 'ID';
$order = 'DESC';
$total_items = $this->get_total_count();
$this->items = $this->get_records( $perpage, $current_page, $orderby, $order );
// echo ''; print_r( $this->items ); echo '
';
// tell the class the total number of items and how many items to show on a page
$this->set_pagination_args( array(
'total_items' => $total_items,
'per_page' => $perpage
));
}
...
MSP_List_Table::get_total_count() :
...
function get_total_count(){
global $mspdb;
$all_items = $this->get_records( 0 );
return count( $all_items );
}
...
MSP_List_Table::get_records() :
...
function get_records( $perpage = 20, $paged = 1, $orderby = 'ID', $order = 'DESC', $where = "status='published'" ){
global $mspdb;
$offset = ( (int)$paged - 1 ) * $perpage;
$orderby = isset( $_REQUEST['orderby'] ) ? $_REQUEST['orderby'] : 'ID';
$order = isset( $_REQUEST['order'] ) ? $_REQUEST['order'] : 'ASC';
$search = isset( $_REQUEST['s'] ) ? " AND title LIKE '%%" . $_REQUEST['s'] . "%%'" : '';
return $mspdb->get_sliders( $perpage, $offset, $orderby, $order, $where.$search );
}
...
MSP_DB::get_sliders() :
...
public function get_sliders( $perpage = 0, $offset = 0, $orderby = 'ID', $sort = 'DESC', $where = "status='published'" ) {
// pull mulitple row results from sliders table
if( ! $results = $this->get_sliders_list( $perpage, $offset, $orderby, $sort, $where ) ){
return;
}
// map through some fields and unserialize values if some data fields are serialized
foreach ($results as $row_index => $row) {
$results[$row_index] = $this->maybe_unserialize_fields($row);
}
return $results;
}
...
MSP_DB::get_sliders_list() :
...
public function get_sliders_list( $perpage = 0, $offset = 0, $orderby = 'ID', $order = 'DESC', $where = "status='published'" ) {
global $wpdb;
$args = array(
'perpage' => $perpage,
'offset' => $offset,
'orderby' => $orderby,
'order' => $order,
'where' => $where
);
return $this->ms_query( $args );
}
...
And finally MSP_DB::ms_query() where actual SQL injection takes place:
...
public function ms_query( $args = array() ) {
global $wpdb;
$default_args = array(
'perpage' => 0,
'offset' => 0,
'orderby' => 'ID',
'order' => 'DESC',
'where' => "status='published'",
'like' => ''
);
$args = wp_parse_args( $args, $default_args );
// convert perpage type to number
$limit_num = (int) $args['perpage'];
// convert offset type to number
$offset_num = (int) $args['offset'];
// remove limit if limit number is set to 0
$limit = ( 1 > $limit_num ) ? '' : 'LIMIT '. $limit_num;
// remove offect if offset number is set to 0
$offset = ( 0 == $offset_num )? '' : 'OFFSET '. $offset_num;
// add LIKE if defined
$like = empty( $args['like'] ) ? '' : 'LIKE '. $args['like'];
$where = empty( $args['where'] ) ? '' : 'WHERE '. $args['where'];
// sanitize sort type
$order = strtolower( $args['order'] ) === 'desc' ? 'DESC' : 'ASC';
$orderby = $args['orderby'];
$sql = "
SELECT *
FROM {$this->sliders}
$where
ORDER BY $orderby $order
$limit
$offset
";
return $wpdb->get_results( $sql, ARRAY_A );
}
...
░▒▓█ Bonus: funny mistake in validation
Plugin: Visitor Maps and Who's Online 1.5.8.6
Idea was good, but something went wrong :-)
function view_whos_been_online() {
...
$show = (isset($wo_prefs_arr['show'])) ? $wo_prefs_arr['show'] : 'none';
if ( isset($_GET['show']) && in_array($_GET['show'], array('none','all','bots','guests')) ) {
$wo_prefs_arr['show'] = $_GET['show'];
$show = $_GET['show'];
}
...
$sort_by = (isset($wo_prefs_arr['sort_by'])) ? $wo_prefs_arr['sort_by'] : 'time';
if ( isset($_GET['sort_by']) && array('who','visits','time','ip','location','url') ) {
$wo_prefs_arr['sort_by'] = $_GET['sort_by'];
$sort_by = $_GET['sort_by'];
}
...
$order = (isset($wo_prefs_arr['order'])) ? $wo_prefs_arr['order'] : 'desc';
if ( isset($_GET['order']) && array('desc','asc') ) {
// bots
$wo_prefs_arr['order'] = $_GET['order'];
$order = $_GET['order'];
}
...

Just a suggestion, but this list would be much more useful to most people if you listed the plugin name first and then the type of vulnerability, and then alphabetized the list.
ReplyDeleteVery nice. The static code analysis tools for PHP are pretty old and useless at this point, and it nice to see someone working to revitalize the area. Have you considered open sourcing your tool? (Possibly through OWASP?)
ReplyDeleteSource code should be published soon or later, because the main purpose of this tool was to inject it in "Continuous Integration" chain. However, codebase is still messy with many experimental ideas and I just don't want to publish it now as it is.
DeleteOn the other hand, publishing it even before your code has "production-grade" quality would still be benefical to a lot ot people, and it would also be the opportunity to have the community help you tidy it up. "Publish early, release often" ;)
DeleteLooks like Plugin Central has been patched
ReplyDeleteYes, thank you.
DeleteP.S. We've added *all* of these to https://wpvulndb.com with links back to this post :)
Delete(patched ones won't show on front page but are in the DB if you look at individual plugin pages)
Great! But there are some wrong dates for "Publicly Published" fields (like in https://wpvulndb.com/vulnerabilities/8325). Public disclosure was 21.11.2015 for all plugins affected.
DeleteVery nice.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteGoods your articles.. Thsk
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeletevery nice site site i like your blog
ReplyDeleteI'm not smart english let alone about computer program but your blog very good thank you
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeletePlease release your tool on github. The PHP static analysis tools OWASP recommend flag false positives that your tool didn't as it is written for Wordpress and I'm guessing picks up on functions like sanatize_email and esc_html
ReplyDeleteЕhe great work you have developed. If you are new, I advise you to consult professionals who will make you a site or allow you to choose a template for your site in the category go here wordpress themes blog
ReplyDeleteCustomer service for me caring for their requirements and helping them and is currently helping anyone who walks into an establishment. Customer service is assisting anyone and meeting with their needs and wants. Good customer-oriented service is just the standard customer-oriented service that everyone is giving to that customer. Good customer-oriented service is if you go out realizing that everything was taken care of with no doubts. Getting individual, helping others the very best that you can. If You Would like to learn More Concerning this topic please Test This out urlhttps://servicecenterguru.com
ReplyDeleteIn this tutorial we'll go through how to get Wordpress running on your own PC (running Windows) so you have your own personal Wordpress installation to experiment with or learn from.https://medijo.lt/etiketes/
ReplyDeleteReally Nice blog, thank you so much for sharing with us. Mobile Apps Development Company Delhi
ReplyDeleteyoutube.com
ReplyDeletehttp://servicehpterdekat.blogspot.com/
http://servicehpterdekat.blogspot.com/http://servicehpterdekat.blogspot.com/
https://storeindonesian.blogspot.com/ https://storeindonesian.blogspot.com/
http://lampungservice.com/
http://lampungservice.com/
http://lampungservice.com/
Tgcindia
ReplyDeleteTgcjaipur
TgceastDelhi
ToursPoints
World Cup is started from 30th May 2019 to 14th July 2019. This world cup is hosted by England.
ReplyDeleteIn this World cup 10 teams is participated & total 48 matches is going to played including 2 semi finals and final.
India and England are strong contenders & favourite
Cricbuzz
Online betting
Who will win
Who will win today
Cricket match prediction
Digital Marketing Institute in Delhi
The previously mentioned advantages alongside different other have made PHP most valuable and famous language for creating dynamic sites. CakePHP Application Development
ReplyDeleteThe PHP content itself is excluded in the HTML that is sent to the program, so the PHP code is imperceptible and secure to the client.Why use Laravel
ReplyDeleteBest Data Science & Machine Learning with Python training institute VisionHook in Noida, Noida, provides real-time and placement oriented Data Science & Machine Learning with Python training in Noida. VisionHook provide the Best Data Science & Machine Learning with Python training course in Noida.
ReplyDeletehttp://www.visionhook.in/best-data-science-and-machine-learning-with-python-training-in-noida.html
Thanks for sharing the valuable knowledge. Also, check out bengali books | buy bengali books | bengali books online | buy bengali books online | best hotel management colleges in kolkata
ReplyDeleteI never comment on blogs but your article is so best that I never stop myself to say something about it. You’re amazing Man, I like it wp database
ReplyDelete... Keep it up
Bagi banyak wanita, mengakhiri kehamilan adalah keputusan yang sulit. Bila wanita tersebut tidak dapat mendiskusikan aborsi atau alternatif dengan penyedia layanan kesehatan, kami menyarankannya untuk membicarakannya dengan teman baik atau keluarga. Kami sangat menyarankan setiap gadis muda untuk berbicara dengan orang tuanya atau orang dewasa lainnya yang dia percayai tentang situasinya, keputusannya dan prosedur aborsi.
ReplyDeleteobat penggugur kandungan di apotik
EduGrowUP has been conceived with the sole objective of bringing technology a step closer to life, more so in the world of education. The identity EduGrowUP in itself is a symbol of our ongoing mission. With over a decade long existence we have been consistently innovating and implementing path breaking ideas. This very objective activated us to build a platform that is available 24 X 7
ReplyDeleteIts really great being a content writer I can understand how tough is it to write and develop the content ,Thanks for sharing this wonderful informationSAP Training in Lucknow Digital marketing training in Lucknow AUTOCAD Training in Lucknow
ReplyDeletePYthon Training in Lucknow SAP FICO Training in Lucknow
PHP Training in Lucknow
http://blog.cinu.pl/2015/11/php-static-code-analysis-vs-top-1000-wordpress-plugins.html
ReplyDeleteSoftware has generally been ensured under copyright law since code fits effectively into the portrayal of a scholarly work.itools virtual location crack
ReplyDeleteChanna Mereya Lyrics
ReplyDeleteWith Brandsoo, it’s never been easier or more convenient to shop high quality domain names and professional logos that’ll instantly give your brand domains for sale a leg up and resonate with your audience! With many different domain sellers all competing for your business, you need to know where your business and brand will see.
ReplyDeleteHey! Grab your 150+ DA 90-50 Google Trusted SEO Backlinks here!
ReplyDeleteThank you!
DigiPeek
CareerCircular Say Thanks For Your Kind Information!
ReplyDeleteSitus judi bola online UFA88 Terpercaya, juga memiliki casino online seperti, baccarat, roulette, Judi slot online, sabung ayam dan dadu online.
ReplyDeletejoker123.ratujackpot.com dan Joker123 merupakan operator Situs Judi untuk permainan mesin slot yang paling terkenal di Indonesia dimana menyediakan Link Login Joker123 secara resmi dan terpercaya serta setiap agen bisa langsung melakukan daftar Akun Slot Joker123 untuk semua member mereka. Selain menggunakan Link Altenatif juga telah tersedia Aplikasi Joker123 APK apabila ingin mendapatkan berbagai kemudahan untuk bisa mengakses dan melakukan Login Joker123 untuk bisa bermain langsung.
ReplyDelete
ReplyDeleteWhether it's a new black lace dress, some sexy lingerie, a brand new pair of shoes, in our online boutique you will find what it is Black lace dresses that you desire! Have Boutique online a look at our collection of Sequined dress fashion dresses and take advantage of our ongoing promotions and discounts! Stand out with one of our Casual dress dresses and turn heads as you walk!
indobet Situs Judi Slot Online Terlengkap 2020 Situs Judi Online populer mendukung deposit Judi Slot Online Deposit Ovo via ovo,gopay,dana, dan linkAja. Segera daftar Judi Slot Online Deposit GoPay di indobet dan klaim promo menariknya Judi Slot Online Deposit Dana.
ReplyDeleteShield Security Solutions Offers Security Guard License Training across the province of Ontario. Get Started Today!
ReplyDeleteSecurity Guard License | Security License | Ontario Security license | Security License Ontario | Ontario Security Guard License | Security Guard License Ontario
We are SEO pittsburgh is a full service internet marketing company in the Pittsburgh area, that specializes in providing affordable internet marketing solutions for small businesses.
ReplyDeleteOur team builds and enhances local business listings and seo search engine optimization. This service drives lead generation and brand recognition.
Our goal is long term mutual relationships with small business owners, providing customized internet marketing services.
I clearly receive your information about what you have explained in this blog.
ReplyDeletewhy crm is important
applications of artificial intelligence in real world
where is python language used
cloud computing certification courses
oracle interview questions and answers
Claim Adjuster - We specialize in helping families with their property damage claim. Take comfort knowing I will do everything I can to help you. Ask for Mike
ReplyDeleteThis was an extremely wonderful post. Thanks for providing this info. Purple Aladdin Vest
ReplyDeleteThanks man for sharing this information. Online classified ads platform in Bangladesh
ReplyDeleteThank You for this valuable information
ReplyDeleteQuikads
"Thank you. I am realy thank you for this post.
ReplyDeletesabung ayam online s128 dan sv388
Tangkasnet
Klik4d
Live22
pragmatic 4d"
AP TET Notification 2021
ReplyDeleteBihar Board 12th Result 2021
Check JAMB Result 2021
Aivivu chuyên vé máy bay, tham khảo
ReplyDeletevé máy bay đi Mỹ Vietnam Airline
chuyến bay mỹ về việt nam
gia ve may bay di Los Angeles
ve may bay tu canada ve viet nam
thanks you very much
ReplyDeletechat
sohbet
نکس وان بت
ReplyDeleteجم بت
انجلا وایت
ولف بت
حضرات
Nice and useful information shared through this post. It helps me in many ways. Thanks for posting this again. Golden Triangle Tour Package India
ReplyDeletenice , hopefully there's much more same as this article .
ReplyDeleteGreat with detailed information. It is really very helpful for us.
ReplyDeleteVillage Talkies a top-quality professional corporate video production company in Bangalore and also best explainer video company in Bangalore & animation video makers in Bangalore, Chennai, India & Maryland, Baltimore, USA provides Corporate & Brand films, Promotional, Marketing videos & Training videos, Product demo videos, Employee videos, Product video explainers, eLearning videos, 2d Animation, 3d Animation, Motion Graphics, Whiteboard Explainer videos Client Testimonial Videos, Video Presentation and more for all start-ups, industries, and corporate companies. From scripting to corporate video production services, explainer & 3d, 2d animation video production , our solutions are customized to your budget, timeline, and to meet the company goals and objectives.
As a best video production company in Bangalore, we produce quality and creative videos to our clients.
Our the purpose is to share the reviews about the latest Jackets,Coats and Vests also shre the related Movies,Gaming, Casual,Faux Leather and Leather materials available Undercover Varsity Jacket
ReplyDeleteสหพันธ์ฟุตบอลระหว่างประเทศไฟเขียวให้ ไอเมอริค ลาปอร์ต ปราการหลังจาก สโมสรฟุตบอลแมนเชสเตอร์ ซิตี้ แห่งศึก ฟุตบอลพรีเมียร์ลีกอังกฤษ เปลี่ยนจากการเป็นตัวแทนทีมชาติ ฝรั่งเศส ไปรับใช้ทีมชาติ สเปน ได้ ทำให้เซ็นเตอร์แบ็ควัย 26 ปีจ่อลงเล่นใน ยูโร 2020 นี้กับทัพ กระทิงดุ... ufa
ReplyDeleteBaccarat is money making plus it's spectacular availability. Optimal In your case it's being sold that you'll find pretty fascinating alternatives. And that is regarded as something that's very different And it's really a little something that's very happy to hit with Likely the most excellent, too, is a very positive choice. Furthermore, it's a really fascinating solution. It's the simplest way which could earn money. Superbly prepar The number of best-earning baccarat is the accessibility of making the most cash. Almost as possible is very ideal for you An alternative which may be guaranteed. To a wide variety of performance and supply And see outstanding benefits as well.บาคาร่า
ReplyDeleteufa
ufabet
แทงบอล
แทงบอล
แทงบอล
Really appreciate you sharing this blog post.Really thank you! Keep writing.m8bet
ReplyDelete良い情報、私は本当にこれに感謝します。ありがとうございました
ReplyDeletem303bet
素晴らしいアーティセル。さらに詳しい情報が必要な場合は、今すぐアクセスしてください。m8bet
ReplyDeleteThank you for this valuable information. I was searching about this.
ReplyDeleteJK Gypsum Decoration is the Best Gypsum Mold Design Agency Dhaka. It has been serving all over Bangladesh for seven years as a Gypsum Decoration & Interior Design Company.
Thank you for your valuable info. Pls keep it update.
ReplyDeleteEcotechnology is a multi-disciplined best environmental consulting firm devoted to providing environmental consultancy services and practical solutions to our clients in Bangladesh.
Partie attrayante du contenu. je viens de tomber sur ton site et dans la capitale de l'adhésion pour affirmer que je reçois vraiment apprécié compte vos articles de blog Sabung Ayam Online .
ReplyDelete<a href="http://51.222.38.194/live22-slot-online/“> Live22 </a>.
Nice read, I just passed this onto a friend who was doing a little research on that.
ReplyDeleteShang Chi and the Legend of the Ten Rings Full Movie 2021
Radhe Full Movie Download 2021
bandar bola online terbesar
ReplyDeletehttps://designingcourses.in/
ReplyDeleteVery Informative and useful... Keep it up the great work. I really appreciate your post.
https://designingcourses.in/graphic-designing-courses-in-bangalore/
https://designingcourses.in/web-designing-course-in-bangalore/
https://designingcourses.in/graphic-design-services/
https://designingcourses.in/online-graphic-design-courses/
I luckily stumbled on your ba 3rd year result date website and I'm really impressed with what I got.
ReplyDeleteYou can save yourself money by purchasing equivalent items from mass merchants. Purchasing decor from a high-end designer can cost lots of money. However, you can typically find similar items without having the brand name of the designer for much cheaper. If you are not able to find an alternative and it is a must have, you can splurge. Hire best gypsum decoration company who can help you for this reason.
ReplyDelete私の知識を増やしてくれてありがとう。私はあなたの記事に本当に感謝しています。
ReplyDeletebolatangkas
Do some research to gain information on the energy sources available to your area. Check the cost of running your home using these utilities, taking into consideration any recent legislation regarding energy costs. For example, it might be wise to use natural gas instead of electric heat or water from the well rather than city water. For any kind of your environmental related get in touch with an environmental service provider.
ReplyDeleteIts amazing information post Fur Leather Jacket
ReplyDeleteHello, thank you for sharing your article with us, and I truly value your information, which I really appreciate, and I would visit your website again.winter jacket
ReplyDeleteTerima kasih atas info terbaik dan tetap berbagi
ReplyDeleteAgen Live Casino
Agen Sbobet
Pragmatic Play
Agen Live Sbobet
nouveaupouvoir
philablazers
soobahkdo
ukiphome
autoandrive
loureedforum
jaga kesehatan dan jangan lupa bersenang-senang
The necessary changes in the role of the security guard and a security company in helping deal with top security companies in London
ReplyDeletethe pandemic have highlighted how imperative security guarding services have been in keeping individuals, businesses, and society, in general, safe and secure. It meant that security guards have had to change their tactics and behaviors to acclimatize to the challenging, changing times.
This is the best post I have ever seen. Very clear and simple. Mid-portion Is quite interesting though. Keep doing this. I will visit your site again. 9th Doctor Jacket
ReplyDeletewhat a great article that you provide us, i need to learn more from you! Cheers. I also doing the same thing here > agen sbobet
ReplyDeleteI read this article. I think You put a lot of effort to create this article. I appreciate your work. Hooper Jacket
ReplyDeleteThis is the geat initiative taken as it makes all the researchers explore new ideas and share their prespective along with their collegues original leather jacket
ReplyDeleteHello, I am Arpita Sinha from Delhi
ReplyDeleteI have Read your post and found it interesting...
Thanks for sharing
Have a Great Day
Graphic design training in Delhi
Very informative article. Would like to read more articles of yours. If you are looking for gallbladder specialist in kolkata visit Clinica Health.
ReplyDeleteI really like you and This information is really very helpful. Thank you for sharing.
ReplyDeleteI will make sure to be reading your blog more. You made a good point Thanks!
if you want to learn UI Development Visit Our Website. https://www.achieversit.com/ui-development-training-course-institute-in-bangalore
Good Info Don't Forget To Visit My Web
ReplyDelete1.Indobola77
2.Sabung Ayam Online
3.Slot Online Live22 Paling Gacor
4.Cara Merawat Taji Ayam Yang Kuat, Mematikan, dan Tak Mudah Patah
Nice Info Don't Forget To Visit My Blog Thank You
ReplyDeleteWAHANAGAMING
Sabung Ayam Online
Jeg vil bare fortælle dig, at din artikel er meget god. Jeg håber du besøger min hjemmeside Tak
ReplyDeletePragmatic Play
Joker123
Join Now http://94.237.70.173/
ReplyDeletegreat article
ReplyDeletehttps://forum138.com
www.forum138.com
DeleteGood News
ReplyDeleteForum138
OBCTOP Adalah situs judi online terpercaya, yang membuka akun taruhan judi bola di bandar judi bola terpercaya dengan bonus cashback sports hingga 10%
ReplyDeleteSlot Online
İnsan böyle şeyler görünce mutlu oluyor
ReplyDeleteWhat would be harder for you, to tell someone you love them or that you do not love them back?# BOOST Your GOOGLE RANKING.It’s Your Time To Be On #1st Page Our Motive is not just to create links but to get them indexed as will Increase Domain Authority (DA).We’re on a mission to increase DA PA of your domain High Quality Backlink Building Service Boost DA upto 15+ at cheapest Boost DA upto 25+ at cheapest Boost DA upto 35+ at cheapest Boost DA upto 45+ at cheapest
ReplyDeletethankyou for this articel, visit my site : daftar judi sbobet
ReplyDeleteVacantology
ReplyDeleteVacantology
Vacantology
Vacantology
Vacantology
Vacantology
Vacantology
Vacantology
Vacantology
Vacantology
It is a nice post to keep sharing valuable information like this.
ReplyDeleteThis comment has been removed by the author.
ReplyDeletelive draw hk
ReplyDeleteIf you need quality SEO Service Bangladesh, Content Writing Services, Graphics Design Services, and Web Development Services, you can count on us. We are here to help your business to be a success! We can expand your business through reaching to the right audience.
ReplyDeleteWE PROVIDE BEST DIGITAL MARKETING COURSES IN DELHI.
ReplyDeleteDigital Marketing Courses in Delhi
we provide digital marketing
ReplyDeletedigital marketing courses in Delhi!
digital marketing courses in Delhi!
ReplyDelete출장샵
ReplyDelete출장샵
출장샵
출장샵
출장샵
출장샵
출장샵
출장샵
OBC4D merupakan situs togel terpercaya dan juga adalah bandar toto hongkong dan totomacau terpercaya dan terbaik di Indonesia untuk saat ini.
ReplyDeleteausmalbilder ostern für kinder und erwachsene bilder zum ausdrucken.
ReplyDeleteThanks for the excellent information you shared I appreciate your efforts and all the best. Thank you for taking the time and sharing this content. It was indeed beneficial.
ReplyDeletevI like your all post. You have done really good work. Thank you for the information you provide, it helped me a lot. I hope to have many more entries or so from you.
ReplyDeleteVery interesting blog.사천출장마사지
양산출장마사지
진주출장마사지
창원출장마사지
통영출장마사지
거제출장마사지
김천출장마사지
문경출장마사지
ReplyDeleteFührerschein kaufen
comprar carta
acheter un permis de conduire
Führerschein kaufen
comprar carta de conduçao verdadeira
comprare patente b
comprare patente vera
comprare patente
buy driver licence
Kann ich einfach sagen, was für ein Trost es ist, eine Person zu entdecken, die tatsächlich weiß, wovon sie im Internet spricht. Habanero Slot
ReplyDeleteCan I simply say what a comfort to discover a person that actually knows what they are talking about on the web. Mahjong Ways
ReplyDeleteI loved this black friday deals
ReplyDeletearticle and kept updating interesting articles
Great Blog!! Really enjoyed the information you provided excellent read positive side black friday sales
ReplyDeletePrediksi Togel Hongkong, Prediksi Togel Sydney, Prediksi Togel WLA paling lengkap cuma disini tempatnya !! Pasti JP Pauss
ReplyDeleteThanks for sharing this post with us. heating masturbator cup
ReplyDeletePretty cool post. It’s really very nice and useful post. William Zabka Cobra Kai Hoodie
ReplyDeleteIt is imperative that we read blog post very carefully.
ReplyDeleteWilliam Zabka Cobra Kai Hoodie
đại lý vé máy bay Eva Air
ReplyDeleteđổi vé máy bay Japan Airlines trước bao lâu
hướng dẫn mua thêm hành lý China Airlines
That’s a really great post. Thanks for sharing with us.
ReplyDeletegraphic design Institute in Delhi
graphic design Training in Delhi
tndte gov in result 2023
ReplyDeletemecidiyeköy
ReplyDeletesakarya
istanbul
kayseri
ordu
2CW
super blog, thanks you
ReplyDeleteErrorcode for family and als error blog.
ReplyDeleteGreat post
ReplyDeleteBroadMind - IELTS coaching in Madurai
Explore the world with Trip Ding! Your passport to adventure awaits. Discover exciting destinations and plan your dream getaway now. Book your dream vacation today and let the journey begin! Cheap air ticket service provider in bangladesh
ReplyDeleteWow! Your blog is a treasure trove of valuable information. The way you articulate complex concepts into easily understandable content is commendable. Keep up the fantastic work. if anyone want to Learn VFX Course with a Deep Level Click Below and Get all the Information
ReplyDeleteKnow the Complete Information about VFX Course in Delhi
çeşme transfer
ReplyDeletekralbet
bor yağı filtre kağıdı
yağ süzme filtre kağıdı
NMZG8M
ReplyDeleteEmbark on a transformative journey into the world of visual effects with Cinemac Animation's VFX Course in Delhi . Learn from industry experts, delve into cutting-edge software, and gain hands-on experience in crafting mesmerizing visual effects. Elevate your skills and unleash your creativity in the heart of India's vibrant animation hub.
Great Blog!! Really enjoyed the information you provided excellent read positive side. animation course
ReplyDeleteGreat blog its very helpful and useful content for us thankyou very much for provided us.
ReplyDeleteYou also should tryTravis Kelce Super Bowl Parade Jacket
Creative article!! This is a very fabulous working style and i hope everyone will like this interesting work page.
ReplyDeleteDiscover the epitome of sophistication with premium black leather shoulder bag Elevate your style effortlessly
ReplyDeleteThanks for providing information regarding PHP and wordpress. If someone looking for the leading social media marketing agency in Delhi to build or grow there business on social media contact now by clicking on the link.
ReplyDeleteThanks for sharing this post with us. java course in noida
ReplyDeletedata analytics training in noida
Thank you for this nice blog python course in noida
ReplyDeleteIt’s a really very nice and useful post. digital marketing course in noida
ReplyDeleteThanks for providing information autocad training in noida
ReplyDeleteBest study abroad consultancy
ReplyDeleteVery Good And Useful information Thank For Sharing if you want join - SQL Database training visit Vcare Technical Institute.
ReplyDeleteRoom coloring pages.18 brand https://ausmalzeit.net new detailed and simple rooms, interior design coloring pages to print and download from larger collection.
ReplyDeleteBest Digital Marketing course in kochi
ReplyDeleteYour post looks impressive and well researched, now I have to look for red motorcycle jacket slim fit in reasonable price.
ReplyDeleteIt's concerning to see that a static code analysis of around 1,000 top WordPress plugins revealed vulnerabilities in 103 of them. This highlights the importance of regular security audits and updates in the WordPress ecosystem to protect websites from potential threats. Developers and site owners should be vigilant about plugin security, ensuring they only use plugins from reputable sources and keep them updated to mitigate risks.
ReplyDeleteSap Training In Muscat
Unlock your potential with our SAP training in Muscat. Tailored for beginners and
professionals alike, our comprehensive courses provide hands-on experience in essential
SAP modules. Led by industry experts, our program ensures you gain practical skills and
valuable certification, empowering you to excel in your career. Join us in Muscat to
take the next step towards becoming an SAP expert and stay ahead in today's competitive
job market.
https://softpro9.com/SAP-Training-in-Muscat/
Maximize your ITC claim with Ai enabled smart reconciliations
ReplyDeletefuhrerscheinfabriskonline
ReplyDeleteköpakörkort
ReplyDeletekupiti-vozakudozvolu
ReplyDeletecumparapermisdeconducere
ReplyDeletekoupitridicskyprukazonline
ReplyDeleteostalaillinenajokortti
ReplyDeleteFantastic work right here on. I review a great deal of article, however I never ever heard a subject such as this. I Love this topic you made concerning the blogger’s pail listing.
ReplyDeleteReader Recipes
This comment has been removed by the author.
ReplyDeleteI always find your posts to be enlightening. This one provided a fresh perspective on a relevant topic.
ReplyDeleteDick Grayson Nightwing Leather Jacket
Your content is always so engaging and thought-provoking. Thank you for inspiring me to think more deeply about these topics!
ReplyDeleteMonica Dutton Yellowstone Black Quilted Jacket
Awesome Content this article Aston Overseas Education Consultants | Study Abroad
ReplyDeleteNice Information for the users:
ReplyDeletebest digital marketing in India
digital marketing company in delhi
Your post looks impressive and well researched. java training in noida
ReplyDeleteDer beste Superblog für Malvorlagen für Kinder und Erwachsene findet ihr hier. Einfacher Bilder aussuchen, herunterladen und ausdrucken! Ausmalbilder Tiere zum Ausdrucken als pdf.
ReplyDeletehttps://permisedeconducerelegale.com/
ReplyDeletehttp://xn--legalerfhrerscheinonline-2sc.com/
ReplyDeletelegalerfhrerscheinonline
ReplyDeletepermisedeconducerelegale
ReplyDeletehttps://permisedeconducerelegale.com/
ReplyDeleteCumpărați un permis de conducere real și înregistrat fără examen.
Permisul dvs. de conducere va fi înregistrat în baza de date și municipalitate,
fără a susține partea practică sau teoretică a examenelor.
https://xn--kupitivoznikodovoljenje-voe.com/
ReplyDeleteThank you for shared good points to here...
ReplyDeleteCheckout the More Furniture Detailed Reviews Online. Check Top List of Wooden Double Bed with Drawers Best Wooden Double Bed with Drawers in India
How to Find the Best Wooden Sofa Come Bed in India with Reviews Best Wooden Sofa Come Bed in India
digital marketing institute
ReplyDeleteBring the classic comedy to life with our Dumb and Dumber suits , now available at Arsenaljackets.com. Inspired by Lloyd and Harry's unforgettable looks, these suits are perfect for adding humor and style to any occasion. Don’t miss out on the chance to rock these iconic outfits.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteThanks for publishing such useful information
ReplyDeleteBest Blog I have ever seen
ReplyDelete"While I see where you're coming from, I think this perspective could benefit from additional data or examples."
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteWordpress is best tool for website, blog and e-commerce.
ReplyDeleteThanks for publishing such useful information. https://www.animationboom.net
ReplyDeleteThanks for publishing such useful information. Animation Course
ReplyDeleteThank you so much for sharing this blog informstion about Wordprees plugins. It's really a very valuable information.
ReplyDeletekupitevozniskodovoljenje
ReplyDeletefuhrerscheinkaufen
best in Kochi
ReplyDeletehttps://cannaverdeshop.com/
ReplyDeletehttps://Papageienparadies.com
ReplyDeletehttps://euhempshop.com/
ReplyDeletehttps://champion-bulldoggen.com
ReplyDeleteA fascinating coloring page for children and adults Ausmalbilder Ostern, these drawings are free. Download a great collection of black and white coloring pages in PDF format.
ReplyDeleteThis is very nice blog
ReplyDeleteautocad training in noida
Cumpara Permis De Conducere online
ReplyDeleteCumpara permis auto
https://xn--cumpraipermisuldeconducere-g5c659e.com
vreau sa cumpar permis de conducere original Aceasta este oportunitatea de care aveți nevoie pentru a obține permisul de conducere românesc original și legal mai rapid și fără proceduri lungi de așteptare.
ReplyDeletehttps://permisdeconducereromanesc.com
carworkshop in dubai
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteGreat information! I wish I had come across this earlier, it would’ve saved me so much time and confusion.
ReplyDeleteCrochet mentioned. "No issue which path it sways https://www.storecws.com/collections/peyton-pallette-jersey, it's out of my manage.
ReplyDelete